Securing Data
A novel technology simplifies secure military communications and has the potential to be beneficial for a wide array of applications.
The Department of Defense (DoD) military strategy relies in part on the development of advanced system technologies that can enable new capabilities for warfighters in the field. For example, imagine the advantages of a new drone or small satellite that can see through foliage and deliver high-resolution, tactical imagery. Because these new technologies are promising, developers focus on creating the systems' major subcomponents quickly, leaving important considerations like cyber security on the back burner. When developers eventually turn to incorporating security features, they often face several complications because they are so far along in the design lifecycle. At this stage, redesigning the system to add security features typically results in crippled system usability, major design delays, superficial security, and large cost overruns.
To address this problem, researchers at Lincoln Laboratory are developing new tools, including a software component known
as the Lincoln Open Cryptographic Key Management Architecture (LOCKMA).1 This software quickly and inexpensively simplifies the task of securing data and communication in a wide variety of systems and may even be employed during later stages of the design cycle.
Cryptography is a vital tool for passing sensitive information to intended recipients and keeping that same information from prying eyes. Through the encryption of data into an unintelligible sequence of characters called ciphertext, a sender scrambles a message with an algorithm and a cryptographic key, and the intended recipient decrypts, or unscrambles, the message by using a symmetric, i.e., used for both encryption and decryption of data, algorithm and key. Though several encryption solutions are widely used to secure data today, they all have one major shortfall: key management.
Key management is the process of generating secure cryptographic keys, making them available to authorized users, and storing them. It is arguably the most difficult aspect of cryptography, says Daniil Utin of the Secure Resilient Systems and Technology Group at Lincoln Laboratory, because developing a new key-management scheme may inadvertently introduce security vulnerabilities caused by system bugs and development oversights. "Developers make key-management systems that combine low-level cryptographic functions into a secure design that supports high-level security functions; it is a complicated process. During the design process, developers can sometimes unintentionally create an insecure system. Even a small bug in the key-management system, such as a biased random number generator that enemies can easily exploit, can create a big security vulnerability," says Utin.
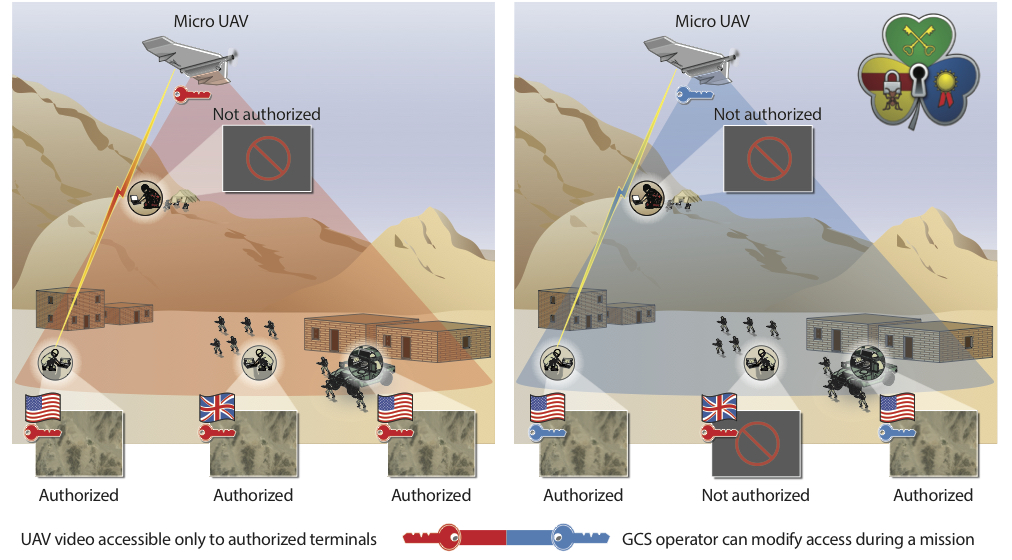
A LOCKMA user can transmit data from a ground control system (GCS) to intended recipients via an unmanned aerial vehicle (UAV) by providing keys to authorized users and can deny access to unauthorized users. The LOCKMA software transmits these authorizations to the intended recipients. |
Some key-management solutions rely on manual key distribution. For example, if two military units plan to send encrypted radio messages to each other, they must first download cryptographic keys onto a Key Processor computer over secure phone lines by using the Electronic Key Management System (EKMS) or over a digital network by using the Key Management Infrastructure (KMI). The units must then manually program the keys into the radio of each communicating device. The key-loaded radios are used for just one mission; if the units need to send encrypted information during a future mission, they must download and install new keys into the radios. This key-distribution process presents several risks, according to Benjamin Nahill of the Secure Resilient Systems and Technology Group. For instance, it may be difficult or impossible for units in the field to access EKMS or KMI. If an enemy captures a unit's radio, the enemy could eavesdrop on communication or impersonate the radio operator. All units involved in the communication must therefore obtain and manually program new keys into their radios. Says Nahill, "It is difficult to ensure that each unit has the correct key, so there is a need for dynamic key management."
Designed to reduce development errors and simplify the key management process, LOCKMA implements storage, organization, and management of key-related information, including key lifecycles, authorized users, and communication channels. Prior to field deployment, each LOCKMA-enabled device undergoes cryptographic provisioning during which LOCKMA generates private keys for each device that will be used in the field. The LOCKMA software uses a public key infrastructure (PKI) service to create certificates that cryptographically bind public keys to individual devices. If a unit wants to securely send a message, it can provide LOCKMA with each intended recipient's device certificate and then use LOCKMA to securely distribute symmetric mission keys and corresponding metadata for message decryption. Because device certificates typically have a lifetime of several years, units can use the same radios for consecutive missions, bypassing multiple journeys to distribution bases. If adversaries capture a radio, LOCKMA will enable the distribution of new mission keys to all authorized radios but the captured one, preventing the enemy from receiving any new communication. The certificate of the captured radio can later be revoked through the PKI.
The military is increasingly relying on the use of unmanned aerial vehicles (UAV) to distribute tactical information. For example, a unit might deploy a UAV throughout mountainous landscape to locate enemy troops or scout tactical locations. The UAV's radio sends a signal back to the unit's ground station, displaying the live video feed from the UAV's camera. However, adversaries are gaining technology to intercept these feeds. To prevent unauthorized video access, LOCKMA can be integrated into the UAV's radio to encrypt the feed and create access restrictions. Using LOCKMA, a unit can identify intended video-feed recipients by their certificates and then send the symmetric key to a group of authorized recipients to decrypt the feed.
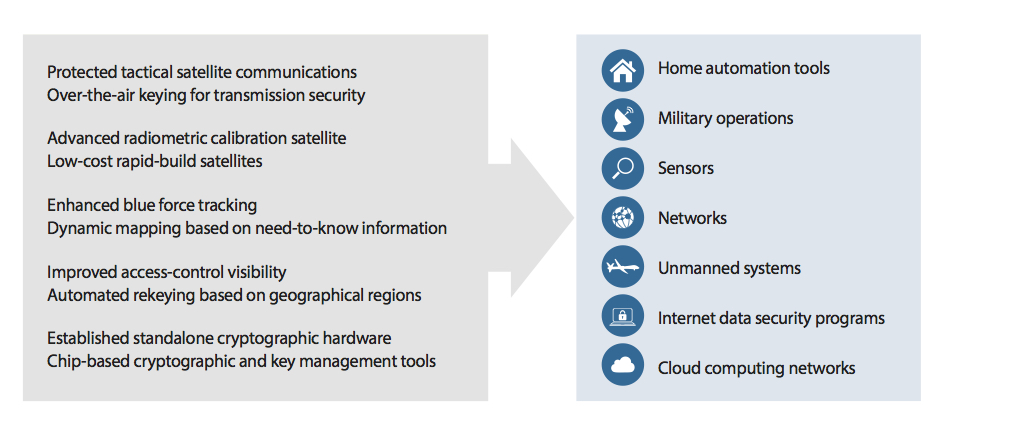
The LOCKMA software can be applied to many applications that require cryptographic key management. Researchers are currently working to develop features (left) that enable LOCKMA to be used in commercial applications (right), such as home automation and cloud computing. |
The Department of Defense is currently working with Draper Laboratory and the National Security Agency to integrate LOCKMA into devices that could benefit from its simplicity, focusing their research efforts on digital radios attached to small tactical devices like UAVs, according to Utin.
LOCKMA's key management messages are based on a cryptographic language standard called Cryptographic Message Syntax, which allows the software to understand and operate seamlessly with most cryptographic algorithms, modes, or key lengths. LOCKMA also works with many operating systems (e.g., Windows, Linux, Android, iOS) and independently, allowing application developers to integrate LOCKMA into devices with minimal changes to LOCKMA's application code.
"Overall, LOCKMA is much more flexible and easier to integrate than traditional key-management systems because, without its holistic approach to security, the entire cryptographic process, from key creation, to management, to delivery, would be much more difficult and error prone," says Utin.
LOCKMA's application programming interface is easy for users to understand even without advanced cryptography knowledge. It hides all cryptographic complexities under the hood, allowing application developers to quickly integrate LOCKMA into devices. The technology saves time and costs compared to a custom key-management system that requires substantial expertise, time, and capital to develop, integrate, and test. Traditional custom-built solutions are also prone to security flaws that are often exploited by adversaries, resulting in substantial additional mitigation and repair costs.
The recipient of a 2012 R&D 100 Award, LOCKMA may become more commonplace as researchers look to integrate it in commercial applications. For example, an increasing number of homes are connecting to "smart" management applications that control energy use and security systems, e.g., Google Nest. Homeowners could use LOCKMA-enabled devices to secure communications within home networks and to thwart hackers. For government organizations, LOCKMA may be useful in tactical operations. "Consider the Boston Marathon bombings," says Utin. "After the attack took place, organizations, including the police and FBI, were communicating over standard shortwave radios. The radios gave anyone, including the suspects, access to those communications. If organizations employ LOCKMA-enabled devices to protect their communications both online and in the field, they can securely provide necessary information to authorized recipients and dynamically accommodate access control changes in real time. LOCKMA really can make a huge difference in national security."
1Lincoln Open Cryptographic Key Managment Architecture (LOCKMA) is available for licensing through the MIT Technology Licensing Office (TLO) under MIT case number 16575L. For more information about LOCKMA and LOCKMA-related patents, contact the TLO at tlo-atto@mit.edu.
|